Background: When a global company is the victim of a ransomware attack, they have to work very swiftly to not only protect their own and their customers’ sensitive data but also their reputation. This is the position a large international provider of B2B software and services found itself in recently following a full-scale, premediated cyber attack. Hackers had locked access to sensitive data and were threatening to go public.
Challenge: Manage the crisis management response to an immediate and ongoing ransomware attack. Support the organisation and the stakeholders impacted by a data breach. Guard the perception of the brand.
Solution: 4C Crisis Management Services ensure a rapid and effective response to a targeted attack on an organisation’s IT system at a strategic and operational level. In this case, we assembled a team of experts, assessed the IT system, advised on immediate crisis management action, and communicated guidelines and action across the organisation.
Benefits: The company was able to mitigate the immediate threat from the attackers and get a complete overview of which data had been breached and how different stakeholders were impacted. Their customers were also provided with support in the form of impact assessments, crisis communication and crisis management directions.
Customer: A global provider of B2B software and services for use in the physical and virtual world.
Cyber attacks – a daily occurrence
Virtually every organisation, whether private or public, faces the very real threat of a cyber attack. These come in multiple forms including:
- Denial of service (DoS) and Distributed Denial of Service (DDoS) in which an organisation’s resources are targeted and its systems are taken offline.
- Ransomware where data is withheld until a ransom is paid.
- Data theft, which unlike ransomware, involves the theft of sensitive data with no intention of returning it.
- Viruses which replicate themselves and are quickly transferred via other code in a system among organisations.
- Phishing, which is a communication-based attack (for example, an email) often sent to an employee from what they believe to be a trusted source.
Crisis management response
Following a recent ransomware attack on a large international provider of B2B software and services, 4C Strategies was assigned with managing the company’s crisis management response. A dedicated 4C team, consisting of crisis management, IT security, and crisis communication experts, was quickly assembled. The initial goal was to ensure the appropriate actions were taken, and – equally important – that the right information and procedures were effectively communicated across the organisation.
“Managing a crisis of this magnitude is like getting on a train in between stations. The perpetrators had planned the attack for months. We needed to act quickly and on multiple fronts simultaneously to limit the effects and take control of the situation.”
Taking control of the situation
According to Klas Lindström, 4C Executive Vice President and crisis management specialist, there are three important tasks that crisis management teams should focus on:
- Getting an understanding of what is happening using a tool such as the 4C Facts and Assumptions Model
- Indicating the way forward for the organisation.
- Ensuring the organisation has the mandate and necessary resources to move ahead
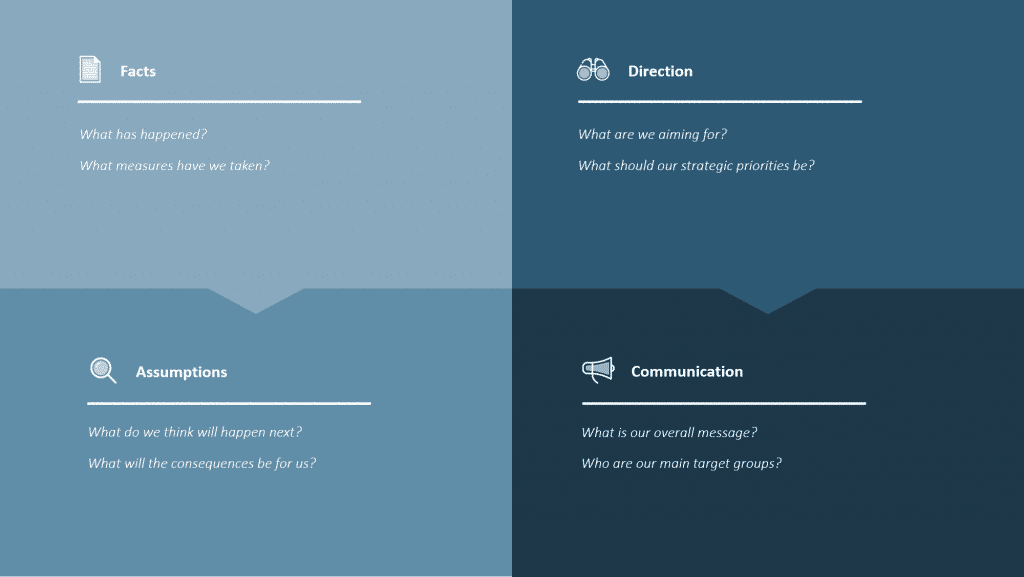
“One of the biggest mistakes we witness are senior managers acting in an operational rather than strategic manner, and mistaking their assumptions for facts,” explains Klas. “This is why we recommend using a proven and intuitive model when dealing with something of this magnitude. The 4C model is a 2×2 matrix used for status reporting and strategic decision-making. It consists of Facts, Assumptions, Direction and Communication, which are continuously updated as the crisis unfolds.”
The 4C Facts and Assumptions Model explained:
- Facts are what we know has happened – no speculation – and what measures have already been taken.
- Assumptions are crucial – they reflect what we do not know for certain, but the way in which the event is likely to develop. They must be verified or reconsidered at every stage of the crisis decision-making process.
- Direction is about what we want to achieve – our goal and strategic priorities, without micromanaging the operational response.
- Communication is about what we communicate, externally and internally, including the target groups for those key messages.
Damage limitation
Damage limitation is always important once it becomes obvious an attack is taking place. When the threat was apparent, the company’s IT team reacted quickly by shutting down servers to limit any damage to a minimum. However, this was just the starting point of what quickly became a full-scale assessment and categorisation of the organisations’ systems and data.
Deploying counter measures
“After the immediate threat of extortion was averted, we began the hard task of further assessing the situation,” explains Johan Würtz, Chief Information Officer at 4C. “This involved conducting an analysis of the data to get a clear understanding of what had been compromised. Based on this analysis, we could deploy effective internal counter measures and advise the company’s clients that had been affected on what actions they needed to take. This consisted of long-term impact assessments, internal and external crisis communications, and general crisis management directions, among other things.”
If you find yourself in a crisis where sensitive data is being targeted there are a number of steps you can take. However, we always recommend you get support from an expert crisis management organisation.
- Disconnect systems where possible and patch up the holes in your architecture
- Identify and map which data has been stolen
- Analyse the stolen data to understand what impact its loss/publication will have
- Implement mitigation plans internally and with customers
- Examine GDPR and any other regulatory repercussions (will vary depending on location and organisation, i.e. government, listed etc.)
- Contact the police, cyber insurance provider and communication specialists
The attack on the company was one of thousands of ransomware attacks that are carried out on a daily basis on multi-national companies. In its 2019-2020 Ransomware Report, ENISA (The European Union Agency for Cybersecurity) found that an estimated 10.1 billion Euros were paid in ransoms during 2019 – a 30 percent rise on 2018 payments. The report also found that although 45 percent of organisations paid the ransom demands, half of them still lost their data.
Read about our collaborations with ENISA.
“4C’s support was key in bringing stability, crisis management experience, IT expertise and carefully crafted communications to a highly volatile situation. The team was always there when we needed them, and we built a strong relationship of trust, availability and action. Having a team that has dealt with this type of incident and all the stages of effective crisis management many times before, gives you the confidence to move forward in your response.”
Prepare for the worst to handle an attack
“The question facing global actors today is no longer if you are a target, but how you will act when an attack occurs,” continues Lindström. “If you haven’t done your risk assessments and practiced realistic scenarios, you won’t be prepared or know how your organisation will cope until it’s too late. How will key staff interact in a high-pressure crisis situation? What systems can and must be turned off? What must be protected at all costs to safeguard operations and sensitive data? What are your strategic directions in a crisis situation?”
“When an attack or a major disruption occurs, you’ll be very happy that you’ve conducted training and exercises in advance, that you have robust IT-systems and contingency plans, and that you have reliable people and partners in the crisis management team,” concludes Lindström.
The spiralling costs of ransomware
The fiscal costs of cyber hacks – before the cost to reputation is calculated – can run into hundreds of millions of dollars. For instance, it’s estimated that the NotPeyta ransomware attack cost global shipping and logistics company Maersk over USD 200 million as, among other things, more than 4,000 servers and 45,000 computers had to be repaired.
Today, cyber security takes multiple forms. Organisations must work proactively to counter the threat of an attack but, in a worst-case scenario, they need proven crisis management processes in place to rapidly manage the situation both from a strategic and an operative perspective. Having effective Business Continuity Management and IT Continuity, will also enable decisions to be taken to maintain critical operations without second-guessing the outcome.
Find out how we can help you prepare with IT continuity planning and response.
A crisis management model to handle uncertainty
4C have developed a simple, fit-for-purpose, crisis management model to establish a solid situational overview for strategic decision-making. The model has been effectively deployed in a diverse range of industries and cultures, from Kuala Lumpur and Bangkok to London and New York.
Discover how you can build your risk, business continuity and crisis management capability with our expert services. Book a free consultation with one of our consultants to discuss your requirements.