This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
What is CIRMP, Critical Infrastructure Risk Management Program?
On Feb 17th The Australian Cyber and Infrastructure Security Centre (CISC) declared that the Critical Infrastructure Risk Management Program (CIRMP) had taken effect and that organizations impacted by it must take the necessary steps to meet and retain the program by August 18, 2023.
As a part of the program, organizations must have documented proof of the controls in place and the plan for mitigating material risks pertaining to critical infrastructure assets. Due to the complexity of selecting and implementing an appropriate cyber security framework at an enterprise level, entities have a further 12 months to meet the CIRMP cyber security framework requirements.
Discover what’s possible with Exonaut
Streamline CIRMP compliance and build resilience capabilities
Who is impacted by CIRMP?
Many–but not all–of the country’s critical assets providers will be impacted by the program and will therefore have to be compliant by August 18th. The relevant sectors are:
- Broadcasting
- Domain name systems
- Data storage or processing
- Electricity
- Energy market operators
- Gas
- Liquid fuels
- Payment systems
- Food and groceries
- Hospitals (designated)
- Freight infrastructure
- Freight services
- Water
What must CIRMP-compliant entities do?
Requirements can be broken down into four steps in a continuous cycle of improvement that must be performed as part of the program:
Step 1
Identify every hazard with a material risk that, should that risk occur, could have a relevant impact on the critical infrastructure asset
Step 2
As far as is reasonably practicable, minimize or eliminate the material risk of the hazard(s) occurring
Step 3
As far as is reasonably practicable, mitigate the relevant impact of such a hazard on the asset
Step 4
Comply and align with other requirements set out in the CIRMP Rules
See Exonaut Resilience in action
4C Strategies provides government, corporate and military clients with a broad range of digital solutions designed to enable capability development, meet compliance, manage training and exercises, and enhance resilience across the organization. Book a free, live demo or meet with one of our expert consultants to discuss your requirements.
Book a demoWhat is a material risk?
-
A stoppage or major slowdown of an asset’s function for an unmanageable period.
-
A substantive loss of access to, or deliberate or accidental manipulation of a critical component of an asset.
-
An interference with an asset’s operational technology or information communication technology essential to the functioning of an asset.
-
The storage, transmission or processing of sensitive operational information outside of Australia, including layout diagrams, schematics, geospatial information, configuration information, operational constraints or tolerances information, and confidential information about an asset.
-
Remote access to operational control or operational monitoring systems of the asset.
These are the material risks as defined in the Critical Infrastructure Risk Management Program, but the list is not exhaustive.
Categorizing critical infrastructure hazards
Critical infrastructure hazards can be categorized into five vectors that are relevant to organizations. The five hazard categories are:
1. General
All hazards are the general processes or systems that must be established and maintained as a part of CIRMP, such as identifying operational context and material risk mitigation plans, as well as the review and management of hazards, assets and their interdependencies.
2. Cyber and information security hazards
This category refers to the establishment and maintenance of processes and systems that minimize any material risk of a cyber and information security hazard occurring or impacting an asset. Within this category, organizations must comply with an appropriate Cyber Security Framework, as outlined in the CIRMP program rules.
3. Personnel hazards
This relates to critical workers / contractors and their access rights to sensitive information. This includes everything from conducting proper background checks to fulfilling thorough and complete off-boarding of employees / contractors to limit the risk of internally-driven disruptions and negligence.
4. Supply chain hazards
Focused on the risk of disruption to critical supply chains, this covers everything from over reliance on suppliers to supply chain interference and exploitation as well as misuse of privileged access and distribution of IP.
5. Physical security hazards and natural hazards
Including anything from unauthorized physical access to critical components / facilities to natural disasters, whereby the risk of these happening and the impact that they can cause should be minimized where possible.
Streamlining CIRMP with a dedicated digital tool
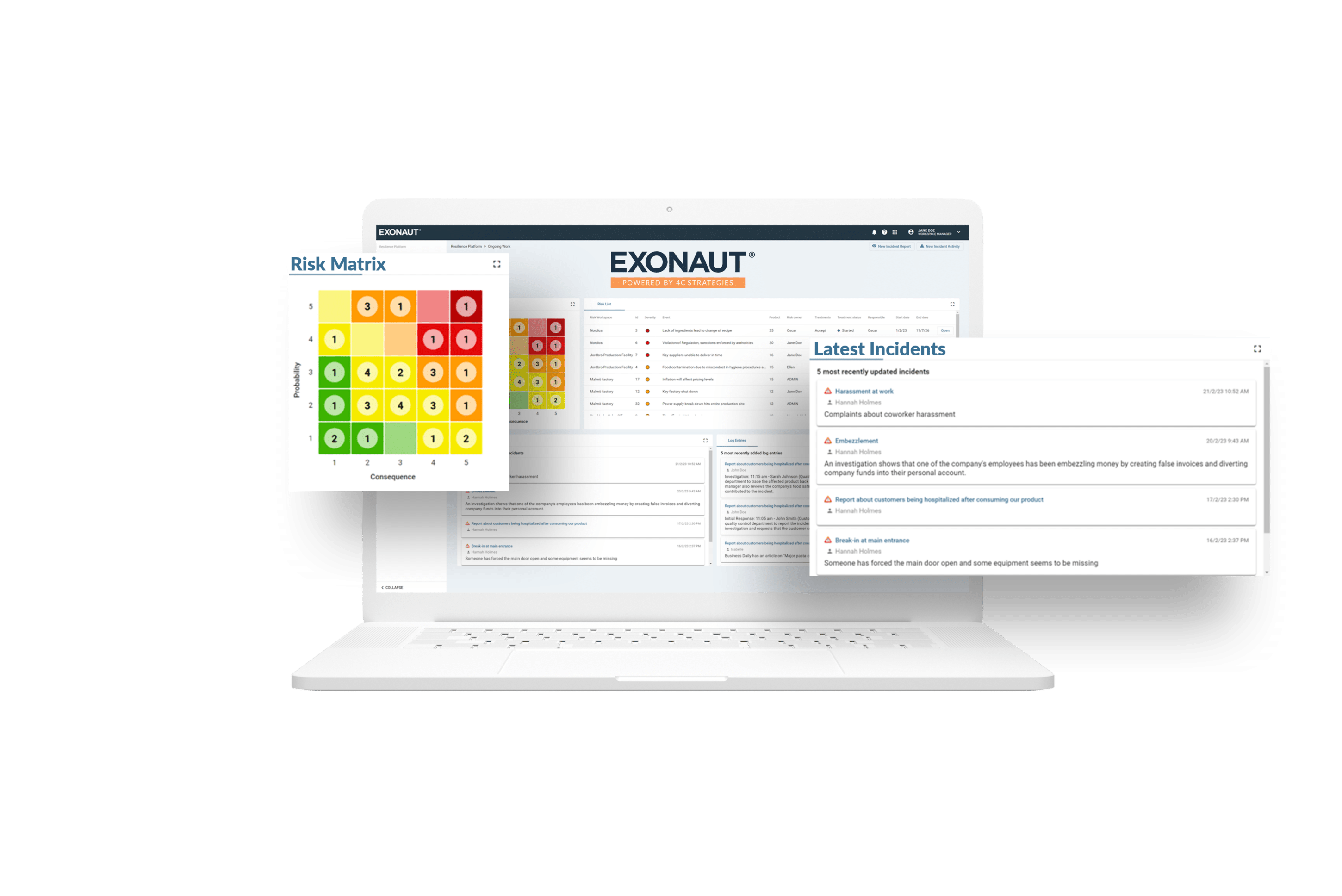
Using a dedicated digital tool for a Critical Infrastructure Risk Management Program enables you to log, categorize, manage, and report critical infrastructure assets, hazards, material risks, and their dependencies. In Exonaut, you can get an up-to-date overview of the current situation or drill down to specific entries.
Risk mitigation and incident recovery plans can be linked to specific hazards and risks. Any actions taken to minimize or mitigate risks can be logged for review. Intuitive, time-stamped reports can be autogenerated at any time, and shared with stakeholders and auditors as part of the compliance process.
Collecting all your data in one, secure system ensures full version control and transparency – something that is typically a problem when using spreadsheets and other make-do systems for reporting. Exonaut’s strict access controls also ensure only the right people can access sensitive data.
A platform approach to resilience
Additional options in Exonaut include training and exercise management, which is ideal for organizations who identify capability gaps as a part of their Critical Infrastructure Risk Management Program, and wish to close them through effective training.
For organizations that wish to connect Risk Management, Incident and Crisis Management or other elements of their organizational resilience program to CIRMP, Exonaut Resilience offers a full suite of products for planning, preparation, prevention, response, and recovery in and integrated platform. This is the industry-leading platform for ensuring you are fully equipped to handle the threats, uncertainties and disruptions that lie ahead.